There have been situations where customer disable un-used ciphers in their server’s infrastructure, only to learn that down the road these ciphers may be needed for the proper installation of Microsoft Defender for Endpoint. As a learned experience, I would like to specify which ciphers are required to get the service installed. (This information is available and confirmed today, June 2023) Microsoft Defender for Endpoint Command and Control channel (winatp-gw-XXX.microsoft.com) only supports TLS1.2 and TLS1.3 with the following cipher suites:
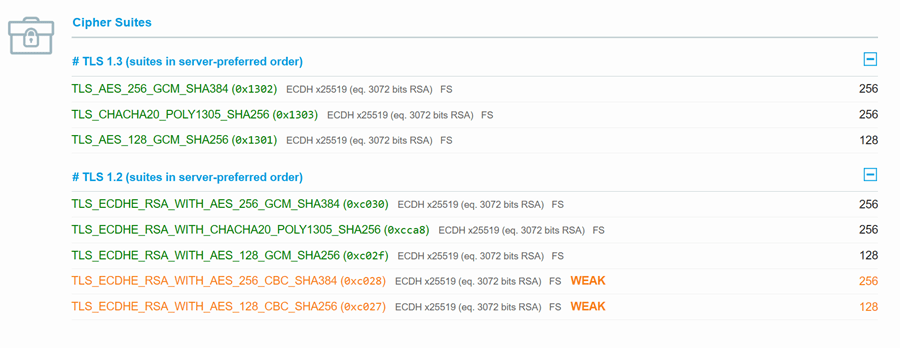
TLS1.3:
- TLS_AES_256_GCM_SHA384
- TLS_CHACHA20_POLY1305_SHA256
- TLS_AES_128_GCM_SHA256
TLS 1.2:
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
EDR Cyber channel URLs only support TLS1.2, with the following cipher suites:
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
These ciphers, are supported in Windows 2012R2: Cipher Suites in TLS/SSL (Schannel SSP) – Win32 apps | Microsoft Learn
Windows Server 2012 R2 are updated by Windows Update by the update 2919355 applied which adds the new cipher suites and changes the priority order.