In the fast-paced digital world, strong vulnerability management is key to solid cybersecurity. Our goal is to equip organizations with top-notch tools and practices to protect their digital assets. Recently, customers have asked about locating the installation path of their vulnerable software in their setups. Using Microsoft Defender for Endpoint (MDE) and Microsoft Defender for Cloud, we can provide this information.
Installation Path Insights
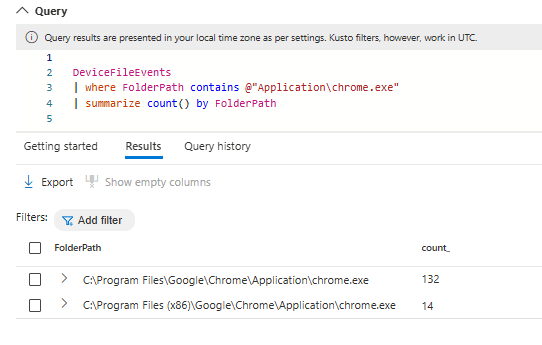
A crucial part of our vulnerability management is offering detailed insights into software installation paths. Microsoft Defender Vulnerability collects this data, which administrators can access via KQL (Kusto Query Language). For example, KQL queries can efficiently find paths for essential software like Chrome.exe. These queries help create thorough summaries for assessing and managing vulnerabilities.
Unified Data Capture

The insights are derived from data collected across all devices utilizing the existing MDE components implemented by our clients. This integrated method guarantees a consistent and thorough understanding of the software environment, allowing us to detect possible vulnerabilities more efficiently. The collected data is easily accessible for querying, giving our clients the ability to customize their vulnerability management strategies according to their unique requirements.
Defender for Cloud Integration
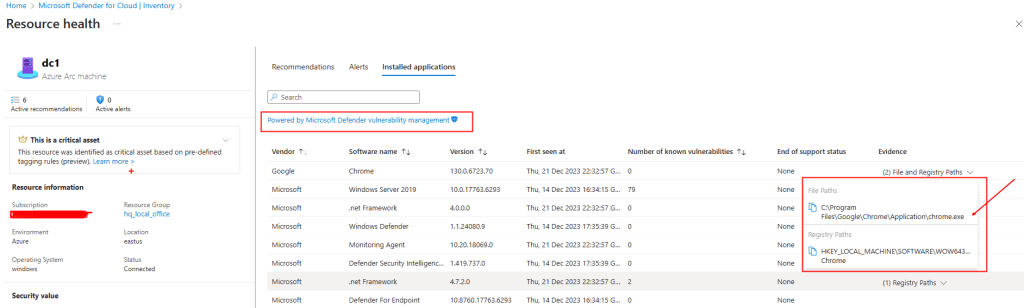
Besides MDE, all servers using Microsoft Defender for Cloud provide detailed insights in the console. This setup uses the same data and sensors as Defender for Endpoint but presents it in a more user-friendly way, improving clients’ capability to track and manage vulnerabilities across their IT systems.
Conclusion
By leveraging the power of Microsoft Defender for Endpoint and Microsoft Defender for Cloud, we empower our clients to proactively manage vulnerabilities and protect their digital assets.