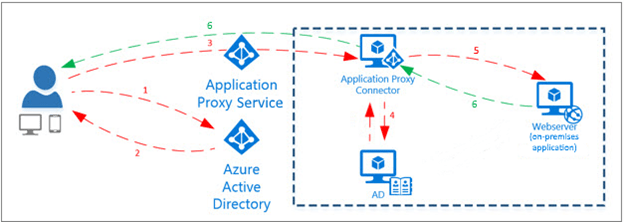
Over the last months, and as we continue migrating our client’s on-premises infrastructure to the cloud, Azure Active Directory’s Application Proxy has become a very power tool used by organization looking into closing their VPN access, migrating workloads to the cloud, and reducing their on-premises footprint. While this is not the final solution for removing the on-premises services, it does serve as a steps to removing the relationship or need of VPN and connectivity to on-premises services, especially for organization that are transitioning from local AD to AzureAD-Joined devices. Azure application provides secure remote access to on-premises web applications. After a single sign-on to Azure AD, users can access both cloud and on-premises applications through an external URL or an internal application portal.
Licenses Requirements: With Azure Active Directory Premium P2 you can gain access to advanced security features, richer reports and rule based assignments to applications. Your end users will benefit from self-service capabilities and customized branding.
Azure AD Application Proxy is:
- Simple to use. Users can access the on-premises applications the same way they access Microsoft 365 and other SaaS apps integrated with Azure AD.
- Secure. On-premises applications can use Azure’s authorization controls and security analytics. Including Conditional Access and MFA. Also, Application Proxy doesn’t require you to open inbound connections through your firewall or VPN.
- Cost-effective. To use Application Proxy, you don’t need to change the network infrastructure or install additional appliances in your on-premises environment.
Install and register a connector
To use Application Proxy, install a connector on each Windows server you’re using with the Application Proxy service.
To install the connector:
- Sign in to the Azure portal as an application administrator of the directory that uses Application Proxy.
- In left navigation panel, select Azure Active Directory.
- Under Manage, select Application proxy.
- Select Download connector service.
- Read the Terms of Service. When you’re ready, select Accept terms & Download.
- At the bottom of the window, select Run to install the connector. An install wizard opens.
- Follow the instructions in the wizard to install the service. When you’re prompted to register the connector with the Application Proxy for your Azure AD tenant, provide your application administrator credentials.
Add an on-premises app to Azure AD
Now that you’ve prepared your environment and installed a connector, you’re ready to add on-premises applications to Azure AD.
- Sign in as an administrator in the Azure portal.
- In the left navigation panel, select Azure Active Directory.
- Select Enterprise applications, and then select New application.
- Select Add an on-premises application button which appears about halfway down the page in the On-premises applications section. Alternatively, you can select Create your own application at the top of the page and then select Configure Application Proxy for secure remote access to an on-premise application.
- In the Add your own on-premises application section, provide the following information about your application:
- Name: The name of the application that will appear on My Apps and in the Azure portal.
- Internal URL: The URL for accessing the application from inside your private network.
- External URL: The address for users to access the app from outside your network. If you don’t want to use the default Application Proxy domain, read about custom domains in Azure AD Application Proxy.
- Pre Authentication: How Application Proxy verifies users before giving them access to your application.
- Azure Active Directory: Application Proxy redirects users to sign in with Azure AD, which authenticates their permissions for the directory and application. I recommend keeping this option as the default so that you can take advantage of Azure AD security features like Conditional Access and Multi-Factor Authentication.
Connector Group: Connectors process the remote access to your application, and connector groups help you organize connectors and apps by region, network, or purpose. If you don’t have any connector groups created yet, your app is assigned to Default.
Best Practices for Azure Application Proxy
- Physically locate the connector server close to the application servers to optimize performance between the connector and the application.
- The connector server and the web applications servers should belong to the same Active Directory domain or span trusting domains.
- Install multiple connector servers on-premises to avoid a single point of failure.
- Configure FQDN and DNS records internally and do not use IP addresses.
- Make sure your connector servers have full internet access and can reach the Microsoft network.
- Use conditional access to secure access to your environment.
- Configure SSO to enhance the end-user experience