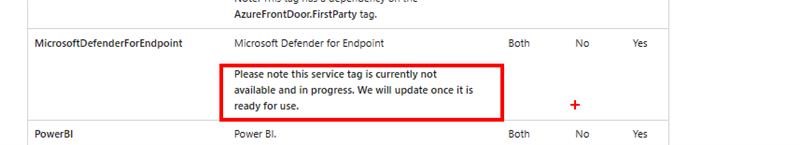
As you may know, NSGs are a vital component of Azure’s security architecture that allow you to filter network traffic based on source and destination IP addresses, ports, and protocols. However, NSGs do not support filtering based on URLs or FQDNs. Although NSGs do offer Service Tags, the Defender for Endpoint Service Tag is not yet available for productions and does not cover all of the Microsoft Defender for Endpoint (MDE) – As of today (May 1st 2023). As shown below. Azure service tags overview | Microsoft Learn
Therefore, I suggest two potential workarounds to implement a solution to allow MDE to connect to the cloud service.
- Configure device proxy and Internet connectivity settings: This workaround requires you to configure device proxy and Internet connectivity settings on the client devices. You can find the detailed steps to configure this on Configure device proxy and Internet connection settings | Microsoft Learn
- Replace NSG with Azure Firewall: Azure Firewall is an advanced security solution that offers FQDN filtering in network rules. It replaces the basic NSG and offers more robust security features. You can find the detailed steps to implement Azure Firewall on Azure Firewall FQDN filtering in network rules | Microsoft Learn
The MDE URLs are specified as required for MDE in the mde-urls.xlsx (live.com) .